Why CyberSecurity Mesh Is Trending in IT?
Why CyberSecurity Mesh Is Trending in IT?
Although digital transformation was on the road map for many companies before the COVID-19 pandemic, it accelerated their efforts. As a result, many companies adopted the necessary technologies to help them support their workforces to work from anywhere.
So, these companies migrated many of their systems and data to the cloud, implemented containerized environments, and invested heavily in connected mobile and IoT devices and platforms. In simple terms, the pandemic required a shift away from on-site computing to a new approach that required distributed systems.
In turn, this new approach to computing requires a new approach to security. This is more so, considering that working from more places creates more threats, with ransomware becoming more prevalent, and hackers being extremely adept at exploiting vulnerabilities and putting companies’ data and systems at risk.
That’s where a cybersecurity mesh comes in and, in this post, we’ll look at it and its benefits in more detail.
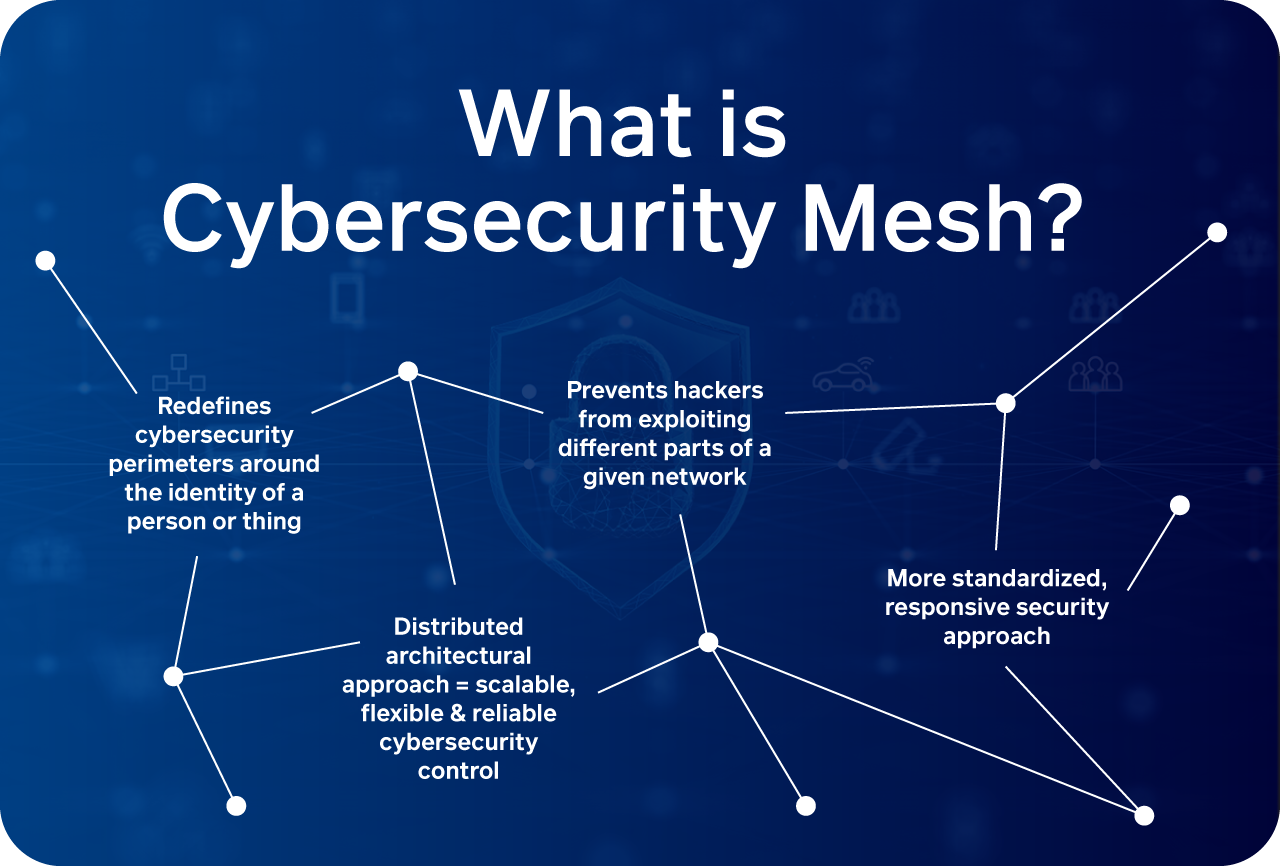
What Is CyberSecurity Mesh?
While there’s no formal definition for a cybersecurity mesh, it’s closely related to the principle of an identity control plane. In other words, it moves away from a traditional perimeter-based approach to security and shifts to a distributed approach where security is focused on the identities of machines on a network, creating individual security parameters for each access point.
A cybersecurity mesh facilitates the centralization of security policies while, at the same time, ensuring that the enforcement of these policies is distributed. This ensures that each access point’s security can be centrally managed which gives companies a robust and flexible approach to manage their cybersecurity when they’re operating from almost anywhere.
How Do You Implement Cybersecurity Mesh?
A cybersecurity mesh approach requires a complete reconfiguration of the security measures on a network. Traditionally, password-protected perimeters used in a ‘walled city’ approach allowed devices to gain access to a network.
So, in other words, when a device gains access to the network, it’s trusted on that network. And this is its biggest downfall, with up to 34% of data leaks and breaches occurring inside the network itself.
A cybersecurity mesh aims to solve this problem by forming a fundamental part of a zero-trust strategy where, by default, no device is trusted to access the rest of the network.
However, successfully implementing a cybersecurity mesh that uses zero trust requires the integration of the different measures during the planning, design and development process of a network.
When this is done correctly, it allows IT systems to adapt to emerging risks, threats, and access needs that change. In turn, the cybersecurity mesh ensures that a company’s data, systems, and equipment are protected and secured equally, no matter where they are located on the network.
The Bottom Line
The COVID-19 pandemic accelerated the digital transformation efforts of many companies. As a result, these companies shifted their computing approach to be more distributed and off-site, which was needed with many employees needing to work from almost anywhere.
This new approach to computing also requires a new approach to security to ensure that all parts of a company’s network are secure and its data protected. That’s where
a cybersecurity mesh comes in. Hopefully, this post helped illustrate what it is and how it’s implemented.